In this blog, I will be detailing how to install Kali Linux, set up a group account, a user account, and to encrypt and decrypt a file. In this fictional scenario, user Jane Doe will be added to the group, Analysts, where she will send an encrypted file (named testfile) via an encrypted email.
Kali Linux is an operating system that is useful for information security tasks, including penetration testing, digital forensics, and security research. I will be using the Oracle VM VirtualBox to run Kali Linux.
The purpose of this blog is to show how to use Linux commands to create accounts and encrypt/decrypt files.
STEP 1: DOWNLOAD VIRTUAL MACHINE AND KALI LINUX
I am using the Oracle VM VirtualBox. This can be downloaded at https://www.virtualbox.org/
Kali Linux can be downloaded at https://www.kali.org/get-kali/#kali-platform (I downloaded the Virtual Machines; VirtualBox 64-bit as recommended)
STEP 2: LOG INTO KALI LINUX AND OPEN THE TERMINAL
The default username and password will be "kali"
Open the terminal; the default password will be "kali"
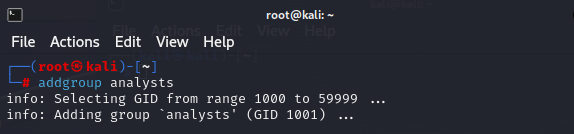
STEP 3: CREATE GROUP ACCOUNT AND ASSIGN USER TO GROUP
Using the addgroup command, I will create a group called "analysts". This command is useful when you need to add multiple users to a specific group. This allows you to create group permissions such as read/write/execute permissions. These three kinds of file permissions are:Read (r): user/group can view a file
Write (w): user/group can write or modify a file or directory
Execute (x): user/group can execute a file's contents
Then I will add Jane Doe as a user to the analysts group, using the useradd -G command. To confirm that Jane Doe has been added, I will use the groups command to confirm the group that Jane Doe is in. You can also look at the group settings to view the users in the group.
STEP 4: INSTALL CCRYPT
Now, I am going to create a text file then use ccrypt to encrypt the file. First, I need to install ccrypt; this is a Linux tool that can encrypt and decrypt a file using a cipher.
To install ccrypt, I am going to type in sudo apt install ccrypt . If you receive an error like I did, type in sudo apt-get update to be able to continue with installing ccrypt
STEP 5: CREATE A FILE
Next, I'm going to create a file using the touch command. The touch command will allow me to create a file that doesn't have any content. Then I will use the ls command to list all files and directories in the directory to confirm that the test file was created.
Using the nano command, I'll add content to the test file.
STEP 6: ENCRYPT FILE
Using ccrypt, I will encrypt the test file. I entered an encryption key, then entered it again to confirm. Now, when you list the contents of the directory using the ls command, you'll see testfile.cpt which confirms that it is now an encrypted file.
Using the ccat command, I will get an output for the file's plaintext content while ensuring the file remains encrypted. Since ccrypt uses symmetric key encryption, the file will be encrypted and decrypted using the same encryption key.
I will change the encryption key by using the ccrypt -x command.
STEP 7: DECRYPT FILE
Finally, I will decrypt the file using the ccrypt -d command. This will allow anyone that has viewing access to see the plaintext content without using the decryption key. I entered the changed key from the previous step. When I list the contents, you will see that "testfile" no longer has .cpt extension at the end of the name, indicatinig that the file is no longer encrypted. This is confirmed when I use the nano command to open the file.
In conclusion, this project used Kali Linux to set up the group "analysts", create the user account "janedoe", encrypt the testfile, and decrypt the file with a changed key. The group was created using the addgroup command. The user was created using the useradd command. I created the file using the touch command and the nano command was used to add plaintext data. Then ccrypt encrypted the file, changed the encryption key, and decrypted the file. This is useful to encrypt files that contain sensitive or confidential information.















Comments
Post a Comment